Making Sense of NIST & Cybersecurity Requirements for Maximo
John Q. Todd, Sr. Business Consultant/Product Researcher, Total Resource Management (TRM), Inc.
Posted 12/28/2023
Cybersecurity Risk Management
It’s all about cybersecurity risk management. No matter if your computing systems are in an on-premises data center, out in the cloud, or down in a mine shaft somewhere, protecting your data and intellectual property from those who wish to nefariously benefit from it is your mission. Managing the risk of intrusion requires a strategy, a framework, and a significant list of tactical activities to keep the baddies away.
NIST Cybersecurity Framework (CSF)
Developed and promoted by the National Institute of Standards and Technology (NIST), the CSF framework helps to organize your approach to cybersecurity risk management. Originally intended to protect critical infrastructure in the US, its methods have been proven to be effective across all industries. It has been adopted by the Federal Government, but also by an increasing number of commercial entities as well.
The framework consists of the following elements for consideration:
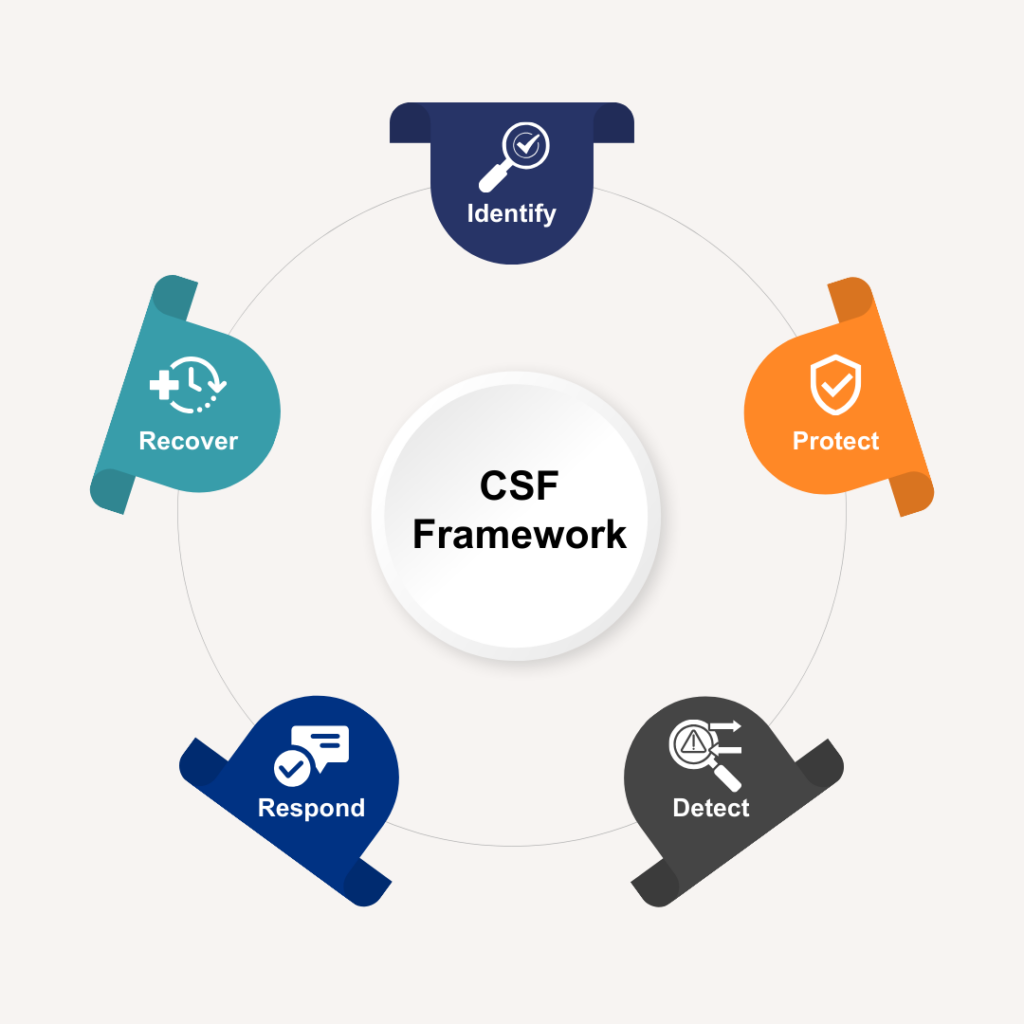
The framework begins with the identification of assets (or resources) that support the critical functions of the organization. Further, risks are associated with these assets of which are the foundation for the risk management approach.
Safeguards are then put into place to mitigate the possibility or impact of a breach. All the while detection is ongoing, looking for activities that are unexpected or out of norms. Responding and recovering to events are also critical elements of the policies and procedures the organization puts into place. Managing incidents from beginning to end, maintaining the continuity of the business or service, and after-action documentation are all important pieces to the strategy the NIST CSF promotes.
An important concept to include in your repertoire of cybersecurity risk management knowledge is that of the Authorization to Operate (ATO). This is the official decision made (or given) that authorizes the information system to be operated and to accept the risks of which are mitigated by the security controls in place.
Every Federal system operated by or on behalf of the Federal government (generally by a contractor) must receive a system ATO. The ATO signifies an acceptance of risk to operate, measured against the applicable standard. An ATO may include “risk accepted” deficiencies which are deemed acceptable risks as it pertains to the system.
What then is NIST SP 800-53?
NIST Special Publication 800-53 is a set of standards developed specifically to assist federal agencies in addressing the requirements established by the Federal Information Security Management Act (FISMA). (Executive Order 13636) While 800-53 is focused on federal agencies, there is nothing preventing a commercial entity to adopt the standards and practices it promotes. All federal systems must comply with NIST SP 800-53.
Adopting standards such as 800-53 are proof of your security maturity vs. that of other commercial operations. You will have increased information assurance via the adoption and practice of standards such as NIST CSF or the more focused NIST SP 800-53.
In general, NIST SP 800-53 includes concerns such as: policy, oversight, supervision, manual processes, individual actions, or automated tasks around information/computing systems. Data storage, processing, and transmission are also covered. It promotes a higher level of detail and complexity than just the NIST CSF.
The NIST frameworks are in constant evolution as the use of web applications, cloud services, and internet connected devices continue to grow at astonishing rates.

NIST SP 800-171
This Special Publication states the requirements for non-Federal systems that process, store, or transmit controlled, yet unclassified information (CUI). Many government contractors handle CUI, so NIST SP 800-171 is an important framework to have in place while executing federal contracts to remain FAR and DFARS compliant.
The publication begins with an assessment approach for an organization to determine how compliant they may already be and where gaps can exist. It also provides direction on how to proceed if one or more requirements do not appear to apply to the organization.
So, what is FedRAMP then?
FedRAMP is the Federal Risk and Authorization Management Program used across the Federal Government to assess, authorize, and monitor products and services in use specifically in the cloud. It consists of a Joint Authorization Board with CIOs from DoD, DHS, and the GSA and a Program Management Office (PMO) for FedRAMP is within the GSA itself.
FedRAMP works with government agencies and cloud service providers to authorize and maintain authorizations so that security packages can be reused by any government agency without re-authorization. It uses a standardized approach to validate and authorize cloud service offerings (CSO). The phrase, “Do once, use many,” can be commonly heard in conversations around FedRAMP.
The process for a CSO to gain approval by FedRAMP consists of selecting the authorization path and security impact level (low, moderate, high), preparing, then going through the authorization process, then continuous monitoring to maintain the authorization. The authorization process is very extensive and can take upwards of a year to complete.
Cloud Service Providers (CSP) who are offering their products (CSO) to Federal Agencies, are encouraged to obtaining FedRAMP authorization. Likewise, Federal Agencies who are looking to adopt cloud-based products and services should consider offerings that are already FedRAMP authorized to ensure a proper security posture.
Certification under any standard requires a Third-party Audit (3PAO) certification upfront and annually to verify the solution satisfies the controls related to each standard. It is crucial to understand the scope of the certification and the requirements. For example, FedRAMP certification can refer to infrastructure only, or the entire application stack.
Numerous Full SaaS offerings are available in the market on the FedRAMP marketplace, such as FedRAMP Authorized Maximo SaaS, which has been assessed end to end – meaning, all related infrastructure, middleware, and the Maximo Application itself. If a solution is FedRAMP authorized, it will be registered on the FedRAMP marketplace at FedRAMP.gov.
The advantage of FedRAMP authorized solutions is that an organization can adopt the ATO that has been given to the solution and avoid taking on this effort on their own, which can be time consuming and costly. The disadvantage is that FedRAMP certified solutions are typically less flexible than on-prem or private cloud solutions and may not permit some of the complexity you require.
Relationship between FedRAMP and NIST SP 800-53
There is a close relationship between FedRAMP and NIST SP 800-53. NIST provides the framework, the guidelines and the controls that FedRAMP Authorized solutions must meet. For simplicity, NIST SP 800-53 is the foundation for FedRAMP controls.
And ISO 27001?
In general, ISO 27001 is the formalization of an information security policy for an organization. It defines what shall be included in an information security management system. It covers 14 areas with 114 controls to consider across the areas.
As with any ISO standard, it outlines the, “what,” not necessarily the “how.” It is up to the organization seeking ISO registration to plan the extent of coverage in the context of what and how the business is operated.
To achieve an ISO registration, an organization will contract with a third-party which will evaluate the effectiveness of the organization at operating the ISO 27001 policies they have established. Auditors look for real proof that all levels of the organization involved are participating as expected.
ISO 27001 does have some overlap with the NIST frameworks, but each stands alone. One cannot say that just because they hold one “certification,” that it covers another. Each must be independently verified to hold any credibility.

Wrap-up – Cybersecurity Risk Management
Which cybersecurity risk management approach or standard you follow can be based upon several factors. If you are a federal government agency or doing business with the federal government, you must comply with FISMA. Specifically for government agencies, your systems must comply with NIST SP 800-53. Most government contractor systems are subject to NIST SP 800-171. Critical infrastructure providers and their suppliers should look to adopt the NIST CSF at a minimum, and potentially NIST SP 800-53. Cloud providers servicing the Federal Government should consider a FedRAMP authorization to make it easier for agencies to use their services.
Any commercial entity can take advantage of these standards to further enhance their own cybersecurity position. Many, not in any category in the preceding paragraph, have chosen to adopt the NIST CSF and/or utilize cloud service providers who are ISO 27001 certified at a minimum. Given the robustness of their implementation, your organization may begin to require your suppliers of cloud offerings and other information systems to be on the path or have already achieved some level of these standards.
For over two decades, TRM has assisted organizations achieve FISMA compliance, including NIST 800-53 and NIST 800-171, for their Maximo systems. In addition, TRM has been instrumental in IBM achieving FedRAMP authorization for the Maximo product line and continues to handle the FedRAMP Maximo SaaS operations. Further, TRM Maximo Cloud Operations is ISO 27001 certified.
TRM’s High Security Cloud for Maximo provides a secure and flexible option for organizations that must meet NIST CSF, 800-53 or 800-171 requirements but require more flexibility than the FedRAMP authorized Maximo Solution can provide.
Reach out to us at [email protected] if you have any questions or would like to discuss deploying MAS 8, Maximo AAM, or Asset Care Essentials (ACE) for condition-based maintenance/monitoring.

John Q. Todd
John Q. Todd has nearly 30 years of business and technical experience in the Project Management, Process development/improvement, Quality/ISO/CMMI Management, Technical Training, Reliability Engineering, Maintenance, Application development, Risk Management, & Enterprise Asset Management fields. His experience includes work as a Reliability Engineer & RCM implementer for NASA/JPL Deep Space Network, as well as numerous customer projects and consulting activities as a reliability and spares analysis expert. He is a Sr. Business Consultant and Product Researcher with Total Resource Management, an an IBM Gold Business Partner – focused on the market-leading EAM solution, Maximo, specializes in improving asset and operational performance by delivering strategic consulting services with world class functional and technical expertise.
Related Articles

The New ISO 12100 – Safety of Machinery

How to Build Your ISO 55001 Asset Management System Quickly and make ISO 55001 Certification Easy

What Do Your Preventive Maintenance Tasks Really Do For Your Asset Care Strategy?

You Think a Computerized Maintenance Management System Is an Option?

Releasing Asset Value Sustainably - An Analysis of ISO55000x

10 Steps to Achieve World-Class Manufacturing Maintenance Practices

Using Effective EAM to Improve Asset Utilization & Reduce Costs

The Key to Unlocking the Full Potential of Your CMMS

How the Industrial Internet of Things (IIoT) Is Shaping Manufacturing

Condition Monitoring in the 21st Century




